Custom Roles in GCP
Introduction
In this project, I explore the creation and implementation of custom roles within Google Cloud Identity and Access Management (IAM).
IAM is a critical component in managing and securing access to cloud resources by defining permissions through roles. Rather than assigning individual permissions, Google Cloud IAM uses custom roles, which simplifies administration and ensures that users are given precise access based on specific job functions by grouping permissions together.
Unlike predefined roles, custom roles allow for a more granular level of control, bundling permissions to create specific access patterns. This flexibility enhances security by ensuring that users only receive the permissions required for their tasks, minimizing the potential attack surface.
Through this project, I demonstrate how to create and manage custom roles, reflecting real-world scenarios where dynamic access control is essential.
Key Learning Outcomes
Creating custom roles to manage user permissionsUpdating roles to include/exclude permissionsViewing available and grantable rolesUsing IAM to ensure cloud security compliance
Role: Junior Cloud Security Analyst
Tools Used: Google Cloud Console, Google Cloud APIs, Google Cloud SDK
Overview of IAM Roles
Predefined vs Custom Roles
Predefined Roles: These are created by the cloud provider and designed for common job functions. While convenient, they often include broader permissions than required for specific tasks.
Custom Roles: These allow organizations to define a unique set of permissions tailored to specific job functions or security requirements, reducing the risk of over-privileged users.
Use Case Example:
For this project, I created two custom roles to demonstrate different methods and use cases:
An “editor” role, built with a YAML file, which provides App Engine version management permissions, and,
a “viewer” role, created with command-line flags, which allows read-only access to specific resources.
In practice, a developer might be assigned the editor role to deploy or roll back applications, while a security analyst could be given the viewer role to monitor logs without the ability to change configurations. This separation of duties enforces the principle of least privilege, ensuring users only have the access necessary to perform their jobs.
Screenshot: Google Cloud IAM dashboard showing predefined roles
Task 1: Viewing Available Permissions
By viewing the current available permissions before role creation, you reduce the risk of overprovisioned accounts, maintain compliance and build more accurate, security focused access controls.
I use the command gcloud iam list-testable-permissions to list permissions. But first I make note of the Project ID as it will be important for the CLI.
gcloud iam list-testable-permissions //cloudresourcemanager.googleapis.com/projects/qwiklabs-gcp-00-6009167a4744
Screenshot: Output of the command showing the available permissions.
Task 2: Get Role Metadata
Role metadata for both predefined and custom roles will help prevent “reinventing the wheel” when it comes to creating custom roles as you can see a full list of included permissions.
The below command produces the metadata.
gcloud iam roles describe role/editor
gcloud iam roles describe role/viewer
Screenshot: Output showing the metadata
Task 3: View Grantable Roles on Resources
Before assigning permissions or creating a custom IAM role, it’s important to know which roles are actually available to be granted on a specific resource. I was able to generate a full list of both Google’s predefined roles and any custom roles that have been created with the following command:
gcloud iam list-grantable-roles //cloudresourcemanager.googleapis.com/projects/qwiklabs-gcp-00-6009167a4744
Screenshot: Output of grantable permissions.
Task 4: Create Custom Role
Now for the meat and potatoes:
This is where I actually create the custom role of “editor”.
First things first, I need to create a role definition YAML file with the command:
nano role-definition.yaml
This opens up a plain text editor in Cloud Shell called Nano where I can define what the role looks like. From the title, description, and permissions needed. The instructions needed to describe the role are as follows:
title: "Role Editor"
description: "Edit access for App Versions"
stage: "ALPHA"
includedPermissions:
- appengine.versions.create
- appengine.versions.delete
Next, I ran the following command to activate the role described in the YAML file we just created:
gcloud iam roles create editor --project qwiklabs-gcp-00-6009167a4744 --file role-definition.yaml
Create Custom Rules Using Flags
Another way to create a a custom role is by using “flags”. Unlike creating a YAML file that describes the new role, the heavy lifting will be done with the actual command.
gcloud iam roles create viewer --project qwiklabs-gcp-00-6009167a4744 \
--title "Role Viewer" --description "Custom role description." \
--permissions compute.instances.get,compute.instances.list --stage ALPHA
Screenshot: This response is the output for the creation of the “viewer” role.
Task 5: List Custom Roles
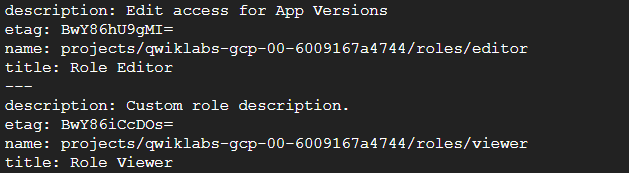
In order to verify that the role I just created has indeed been created and readily available I use the following gcloud command:
gcloud iam roles list --project qwiklabs-gcp-00-6009167a4744
Screenshot: Output of listed custom roles.
Task 6: Updating a Custom Role Using YAML File
The following gcloud command displays the current definition for the rule:
gcloud iam roles describe editor --
project qwiklabs-gcp-00-6009167a4744
Screenshot: Displays the description of the “editor” role.
I ensure that I copy the output of the roles description to paste in the new YAML file and add the following new permissions under “includePermissions”
- storage.buckets.get
- storage.buckets.list
nano new-role-definition.yaml
Screenshot: Displays what the YAML file will look like after placing the new permissions
The following update command will activate the new permissions for the “editor” role:
gcloud iam roles update editor --project qwiklabs-gcp-00-6009167a4744 \
--file new-role-definition.yaml
Screenshot: Displays the output of the successful updated permission.
Updating Custom Rule with Flags
The --permissions flag is the command that is used to specify the new permissions. Here I will show how I added the same permissions as I did with the updated permissions for the “editor” role.
- storage.buckets.get
- storage.buckets.list
gcloud iam roles update viewer --project qwiklabs-gcp-00-6009167a4744 \
--add-permissions storage.buckets.get,storage.buckets.list
Screenshot: Output of the successful update of the new permissions to the viewer role.
Conclusion
Summary
IAM custom roles are an essential tool for enforcing granular access control in modern cloud environments. While predefined roles serve general use cases, they often include excessive permissions, posing security risks. Custom roles empower organizations to define specific permissions that align with both job responsibilities and security requirements, ensuring compliance and reducing potential attack vectors. By strategically implementing custom roles, organizations can better adhere to the principle of least privilege, optimize security, and maintain operational efficiency.
Key Takeaways
Granular Access Control: Custom roles allow precise control over permissions, aligning access levels with specific job functions.
Enhanced Security: By limiting permissions to only what’s necessary, custom roles significantly reduce the risk of over-privileged users and potential security breaches.
Operational Efficiency: Tailored roles prevent unnecessary access, reducing the complexity of permissions management and improving clarity in access control policies.
Flexibility: Custom roles offer the flexibility to adjust permissions as organizational needs evolve, making it easier to scale securely within cloud environment